InInformation Security Policy

1.Basic Policy on Information Security
In order for Kyoto University of Advanced Science and Technology (hereinafter referred to as “the University”) to enhance its academic research and educational activities in the advanced information society, it is essential to ensure the security of the University’s information assets in addition to the maintenance of its information infrastructure.
In order to make all members of the university fully aware of the importance of information security and to firmly protect information assets, the Information Security Policy (hereinafter referred to as the “Policy”) has been established.
2.Definition of Policy Terms
| 1. | Information Security | Maintaining confidentiality, integrity, and availability of information assets. |
| 2 | Information Assets | A general term for information and information management mechanisms (Information systems and data for system development, operation and maintenance). However, unless otherwise specified, information assets are limited to those related to information systems. |
| 3 | Information system | A system that consists of hardware, software, networks, and recording media within the same organization, and that performs business processing as a whole. |
| 4 | Standards for Information Security Measures (Hereinafter referred to as “measures standard”.) | Standards for acts and judgments to be complied with to ensure information security, that is, what must be done to realize policies. |
| 5 | Implementation Procedures (Guidelines) | Standards that indicate the procedures to be followed to implement the content specified in the Standards for Information Security Measures for each subject. |
| 6 | Departments | Faculty, Graduate School, and secretariats (divisions, offices, etc.). |
3.Scope
In addition to KUAS’s information assets, the scope of the policy includes KUAS computers temporarily connected to KUAS’s network.
The scope of the policy is faculty and staff, Temporary Employee, part-time faculty and staff, contract faculty and staff, contractors, graduate student, university students, research students, subjects, auditor, contractors, visiting scholars, etc., who are authorized to use KUAS’s information systems.
The scope of the policy shall be recognized and complied with by.
4.Disclosure of Policies, etc.
Policies shall be disclosed.
Standards for Measures shall be disclosed to Information Security Management Committee Committee Member and Information and Communication Technology Center staff.
Implementation procedures (guidelines) shall be disclosed to the relevant persons.
Disclosure procedures shall be in accordance with Information and Communication Technology Center’s provisions.
5.Organization and System
5.1 Structure of Management and Operation Organization (Figure 1)
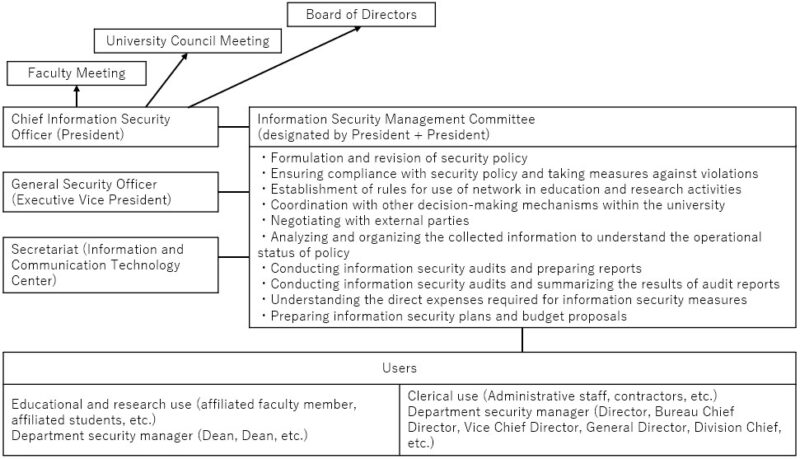
5.1.1 Chief Information Security Officer
KUAS has a Chief Information Security Officer, who is assigned by President.
The Chief Information Security Officer has overall authority and responsibility for information security at KUAS.
5.1.2 University-wide Security Manager
KUAS has a University-wide Security Manager at KUAS, who is assigned by Executive Vice President.
The University-wide Security Manager assists the Chief Information Security Officer in comprehensive responses, including emergency communications, regarding the implementation of information system management at KUAS.
5.1.3 Departmental Security Managers
KUAS has a Departmental Security Manager at KUAS, who is assigned by the following persons.
- The Dean of each department and the Dean of each graduate school
- Bureau Chief Director, Vice Chief Director, General Director, Division Chief, and General Office Director
The Departmental Security Manager is responsible for the following matters managed by the Department.
- Management of Information Equipment under Control
- Disclosure and non-disclosure of Information Assets under Control
- Prevention of falsification of Information under Control and dissemination of false Information
- Disposal of Information Equipment under Control and Storage Media
- Understanding of Operational Status of Policies of Users under Control
- Other Matters Related to Information under Control
5.1.4 Information Security Committee
Information Security Management Committee is located in KUAS and consists of the Chief Information Security Officer, the University-wide Security Manager, and a few persons designated by the Chief Information Security Manager.
The chairperson of the management department is located in Information Security Management Committee, and the Chief Information Security Manager serves as the chairperson.
The deputy chairperson of the management committee shall be the University-wide Security Manager, and when the management committee is unable to perform its duties due to school duties or other reasons, he/she shall perform his/her duties on behalf of the management committee.
The chairperson of the management committee shall convene Information Security Management Committee and serve as the chairperson.
When the chairperson of the management committee deems it necessary, he/she may request the attendance of the department security manager and hear his/her opinion.
The secretariat shall be Information and Communication Technology Center, and shall provide liaison and coordination and support for the security management of the information system of the entire university.
Information Security Management Committee shall deliberate on the following matters.
- Formulation and revision of policies
- Encouragement for compliance with policy and measures against violations
- Audit of policy implementation
- Formulation and revision of measures and implementation standards
- Establishment of intramural rules on information security and implementation of awareness and education
- Coordination with other decision-making mechanisms within the university.
- Negotiation with external parties.
- Audit of policy operation
- Emergency response
- Other important information security matters
5.2 Responses to Unauthorized Access, etc.
When Information and Communication Technology Center detects unauthorized access from outside or inside, it shall shut down the relevant communications or disconnect the relevant information equipment in accordance with the emergency procedures established by Information Security Management Committee. However, the Chief Information Security Officer shall make a judgment in cases where the procedures are not specified in advance.
If unauthorized access continues, Information Security Management Committee shall take deterrent measures such as stopping the regular use of the relevant information equipment or the network connecting it.
6.Management of Information
Information stored in servers is managed by the department security manager, and is managed by must. Information in computers that are privately managed is managed by the department security manager and users of those computers.
6.1 Access Restrictions
may defines users who can access information according to the content of information.
Users must not attempt to enter information systems or information to which they do not have access rights. If users enter information unintentionally, they should be made aware of it so that they can leave the information as soon as possible.
Access can be restricted by ID and password, IC card, etc.
6.2 Classification of Information
6.2.1 Non-public Information
Non-public information must not be stored on computers by anyone other than authorized personnel. In addition, non-public information must not be reproduced on computers used by faculty and staff on a daily basis, even temporarily, in a manner that is readable by unspecified persons.
Networks handling non-public information must be logically different from general networks for academic research and education, and encryption and wiretapping prevention measures should be implemented.
If access is required between the general network and the private information network, must will only allow access from the private network. In addition, the number of connection points between the two networks should be kept to a minimum, and if possible, it is desirable to have a shall that allows communication only when necessary.
In order to prevent physical theft, etc., non-public information must not be taken outside from the authorized places.
Similarly, to prevent eavesdropping, access to non-public information in a form that can be intercepted by unspecified persons via public lines such as the Internet is prohibited in principle.
If it is necessary to disclose non-public information to a limited third party for outsourcing, etc., a confidentiality agreement must be signed each time the information is disclosed.
6.2.2 Public Information
Since public information can be accessed from any location, the preventive measures listed in 2.3 should be taken against falsification of information and dissemination of false information.
6.2.3 Outgoing information (push mails, etc.)
As with public information, it is necessary not only to take the preventive measures listed in 6.3 but also to prove that the sender is a legitimate person.
6.3 Making information public
When making non-public information public, it is necessary to extract only the information that can be made public, or to process such information as statistical processing, paying sufficient attention to leakage of personal information and invasion of privacy and copyright.
6.4 Limited disclosure of information
When it is necessary to disclose specific information to specific users, must provides authentication and access control functions so that authorized persons can register and view information only for authorized operations. In addition, must periodically checks the status for abnormal registration and browsing.
6.5 Prevention of falsification and dissemination of false information
The originality of non-public and public information shall be guaranteed by, for example, storing the originals on non-rewritable storage media such as CD-ROM/CD-R.
On the other hand, countermeasures against falsification of public information shall be taken by must against the ever-evolving threat of unauthorized access technology, and must shall provide a mechanism for quick recovery in case of falsification. In addition, efforts must be made to maintain the originality of public information (including information posted on the Web and information disseminated through e-mail magazines) in order to prevent the creation and dissemination of false information by copying and adding. Therefore, it is desirable to consider the introduction of electronic signatures.
6.6 Disposal of Information Equipment and Storage Media
When disposing of information devices and storage media, regardless of whether they are open or closed to the public, must shall take care of the disposal method. In particular, due consideration should be given to the fact that only the management information is erased and the data itself is not erased by a normal erase operation with respect to storage media such as hard disks and floppy disks, and that the information can be restored by reading out the residual magnetic information by several overwrite erasures.
In addition, when replacing the storage media of information devices under a maintenance contract or removing rental equipment, due consideration should be given to the processing method of the storage media after removal.
7.Evaluation and Review
7.1 Policy Operational Status
The Chief Information Security Officer shall request Information Security Management Committee and Information and Communication Technology Center to take the following measures in order to understand the Policy Operational Status, etc.
7.1.1 Understanding the Policy Operational Status, etc.
The University-wide Security Officer shall periodically hold Information Security Management Committee meetings, analyze and organize the collected information, review the policy periodically and as needed based on the Policy operational status of the entire university obtained through the Departmental Security Officer, and recognize the incompleteness of the Policy.
7.1.2 Opinions of Users
The University-wide Security Officer shall collect opinions on policy compliance from faculty and staff and students, report them to Information Security Management Committee, and report them to.
7.1.3 Information Security Diagnosis
The University-wide Security Officer shall conduct information security diagnosis of information systems from the viewpoint of confidentiality, integrity, and availability of information systems and crime prevention, report the results to Information Security Management Committee, and compile the information security diagnosis to must.
If a serious security vulnerability is found during the diagnosis process, take emergency evacuation measures, promptly report the fact to the Department Security Officer and Information Security Management Committee, and promptly report it to the Chief Security Officer.
7.1.4 Information Security Audit
The University-wide Security Officer shall conduct periodic audits and unannounced audits to ascertain whether each department complies with laws and regulations, policies, and related regulations and standards. The results of the audits shall be reported to Information Security Management Committee, and the results of the information security audits shall be compiled into.
7.1.5 Security Measures Expenses
Information Security Management Committee has identified the direct cost of information security measures, and must. include the cost of equipment purchased to detect unauthorized access, etc. (Including hardware, software, and software upgrades), anti-virus software, and outsourced security diagnostics and audits.
To maintain information security, it is essential to correctly estimate the cost and take budgetary measures. It is unacceptable to neglect serious information security vulnerabilities due to lack of budget.
7.2 Measures to Improve the Security Level
The Chief Information Security Officer shall convene with Information Security Management Committee at least once a year to assess the extent to which measures in accordance with the policies have been implemented and to take necessary measures to improve the security level.
7.2.1 Updating the Policy
Based on the results of 7.1, Information Security Management Committee shall evaluate the effectiveness of the policies at least once a year, review the necessary parts, change the content and decide on the implementation timing, and update the policies to have a higher security level and to be compliant with
7.2.2 Preparation of Information Security Plan and Budget Proposal
Based on the results of the evaluation and review, Information Security Management Committee shall prepare the information security plan and budget proposal for the next fiscal year.
7.2.3 Duty to Report
The Chief Information Security Officer shall report the results of the evaluation and review to the highest decision-making organization (Board of Directors, the Council, Faculty Meeting, etc.) in must. Furthermore, the summary of the evaluation and review shall be presented to the users in order to enlighten the compliance with the policy.




